JWT versus PASETO
Two token-based authentication mechanisms
Authentication is one of the most critical parts of building secure applications. Over the past decade, token-based authentication has become the go-to method for web and mobile systems, allowing clients and servers to communicate securely without constantly re-checking passwords.
For years, JWT (JSON Web Tokens) has been a popular choice in this regard. More recently, a new standard called PASETO (Platform-Agnostic Security Tokens) has also emerged, offering improvements in both security and simplicity.
So, what’s the difference between JWT and PASETO, and when should you use one over the other?
Let’s break it down.
JWT
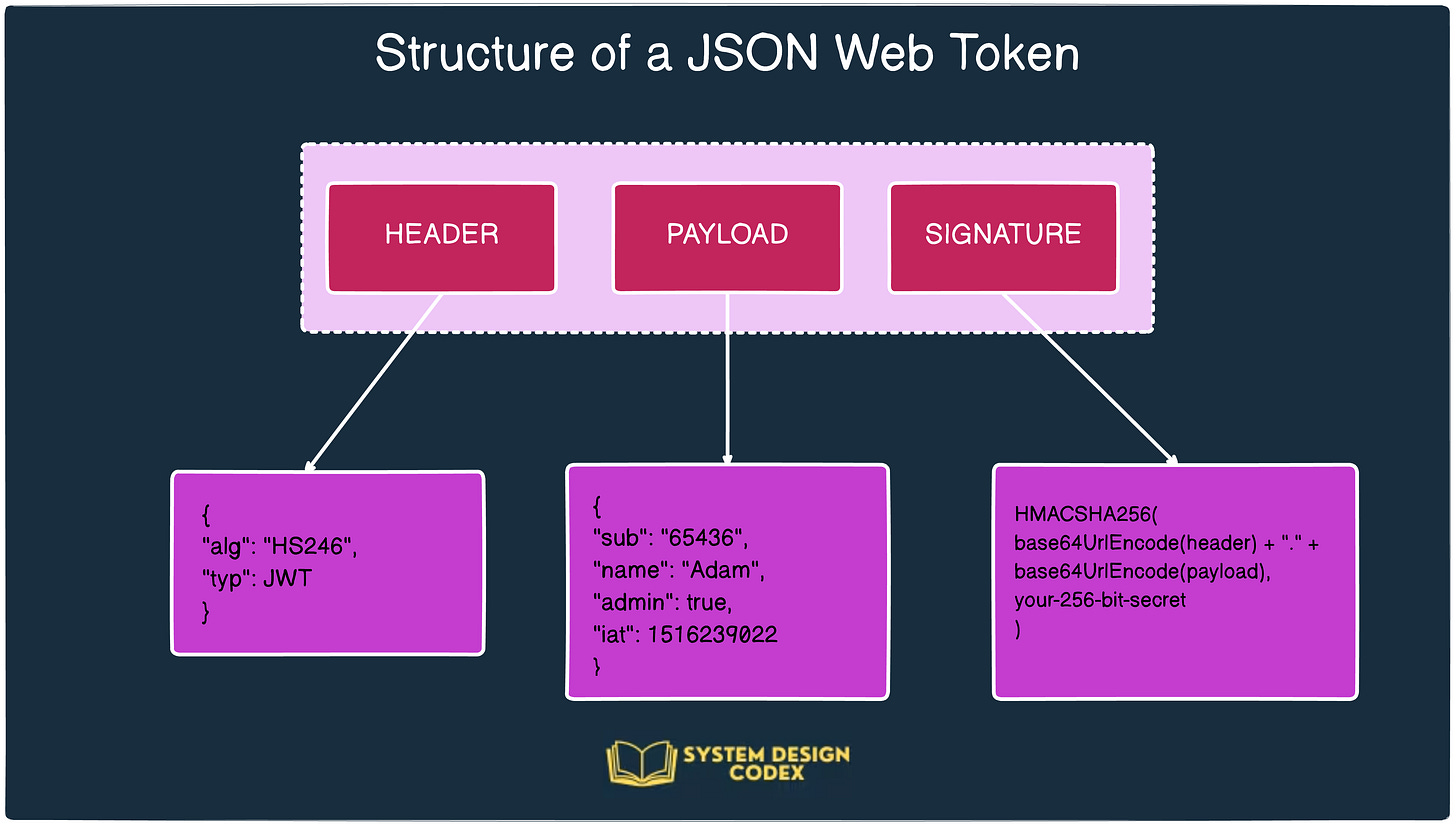
A JSON Web Token (JWT) is an open standard (RFC 7519) designed to transmit information securely between two parties as a compact, URL-safe token.
A JWT has three main parts:
Header – Specifies the algorithm and token type.
Payload – Contains claims such as user ID, roles, or expiration times.
Signature – Ensures the token hasn’t been tampered with, generated using the header, payload, and a secret key.
Example (simplified):
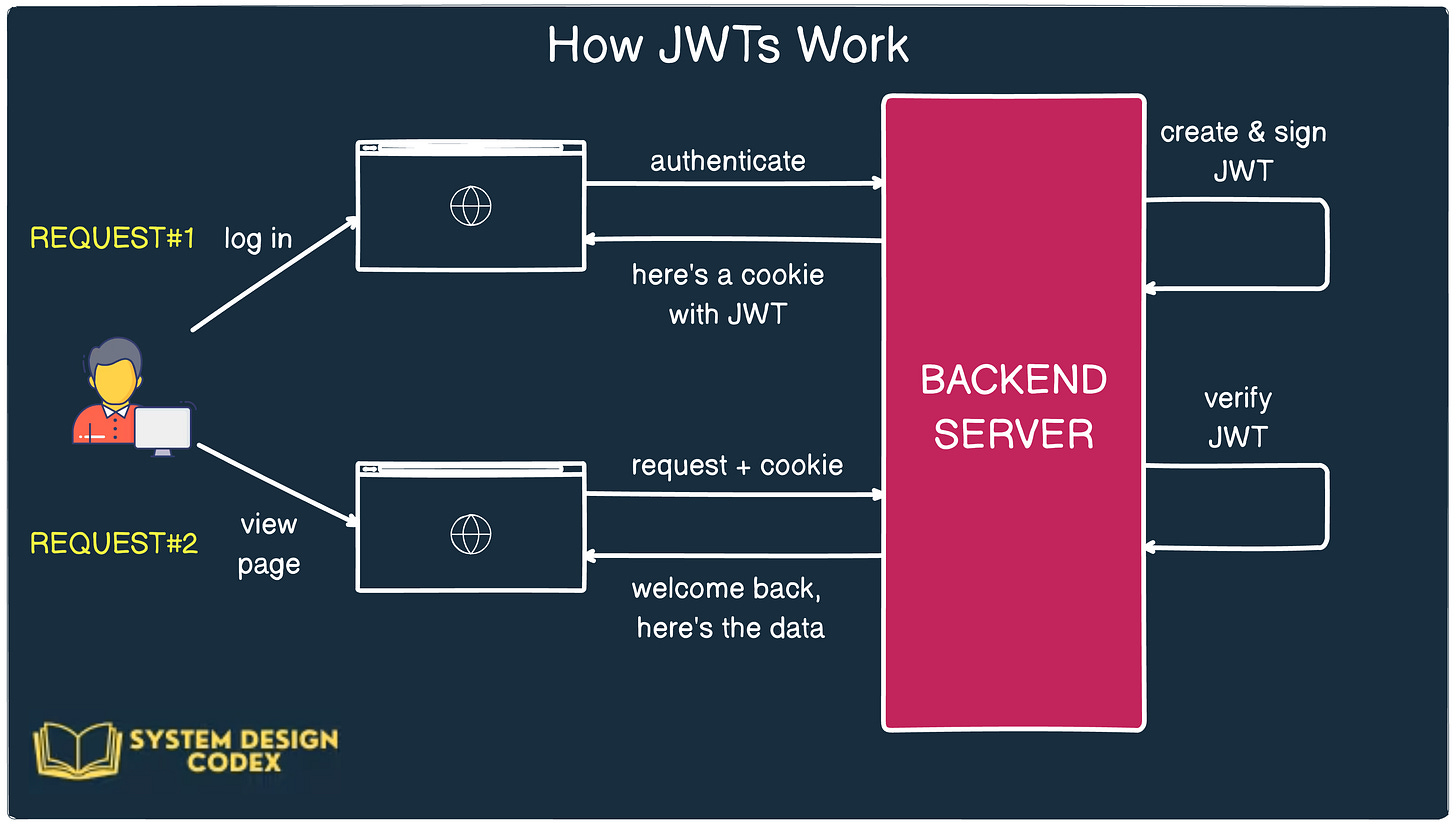
xxxxx.yyyyy.zzzzzHow it works:
The server generates a JWT after successful login and sends it to the client.
On subsequent requests, the client includes the token in its headers.
The server validates the token’s signature before granting access.
Why JWTs are popular:
Stateless authentication: No need to store sessions on the server.
Compact format: Easy to pass in URLs or headers.
Flexibility: Can include custom claims like permissions or roles.
Drawbacks of JWTs:
Algorithm confusion attacks: Because JWT allows multiple signing algorithms, developers might misconfigure them (e.g.,
nonealgorithm vulnerability).Complex security choices: Developers must choose algorithms carefully; insecure defaults can lead to serious issues.
Large tokens: Adding too many claims can bloat tokens, hurting performance.
Despite these challenges, JWT remains widely used in APIs, microservices, and mobile applications.
PASETO
Platform-Agnostic Security Tokens (PASETO) was designed as a simpler and safer alternative to JWT. It keeps the core idea of transmitting claims in a compact token but avoids some of JWT’s pitfalls.
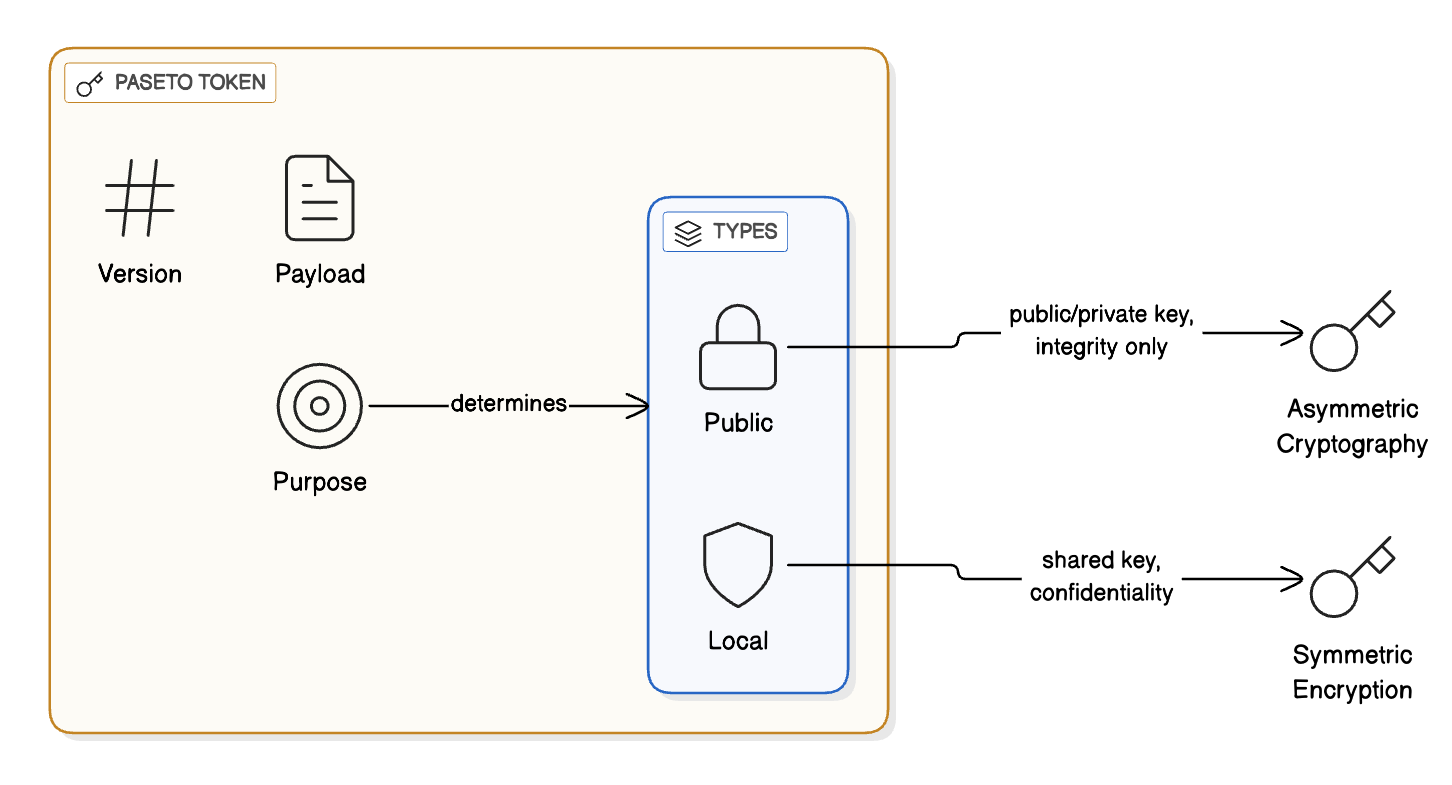
A PASETO token has three parts:
Version – Indicates which PASETO version is being used.
Purpose – Defines whether the token is for public or local use.
Payload – Contains the claims (like user data).
Two types of PASETO:
Public PASETO – Uses asymmetric cryptography (public/private key pair). It guarantees the integrity of data but not confidentiality.
Local PASETO – Uses symmetric encryption (a shared key). It ensures confidentiality as the payload itself is encrypted.
Why PASETO is considered safer:
Secure defaults: Unlike JWT, you don’t choose an algorithm. PASETO enforces modern, strong cryptography (e.g., AES-256-GCM, Ed25519).
Simpler spec: No room for algorithm confusion attacks.
Reduced developer error: By design, it removes insecure options.
Drawbacks of PASETO:
Smaller ecosystem: JWT has been around longer and has more libraries, tooling, and community support.
Less adoption: Many frameworks natively support JWT but not PASETO (yet).
Final Thoughts
JWT and PASETO both solve the same problem: enabling stateless, token-based authentication. JWT has the advantage of maturity and adoption, but it comes with pitfalls if developers don’t choose secure algorithms or configure it correctly.
PASETO, on the other hand, attempts to take a modern, opinionated approach, removing insecure options and enforcing strong cryptography. While it’s newer and not yet as widely adopted, it’s gaining attention for its simplicity and focus on safety.
So, have you tried JWT or PASETO in your projects?
Shoutout
Here are a few interesting articles I read last week:
That’s it for today!
Enjoyed this issue of the newsletter?
Share with your friends and colleagues.


Good comparison, Saurabh.
PASETO is a step in the right direction; safer defaults, less foot-gun risk.
But adoption is still low, and JWT’s inertia is hard to beat.