6 Strategies to Build Secure APIs
An insecure API is bad business
An insecure API can expose sensitive data, compromise your application, and open the door to attacks such as unauthorized access, data breaches, and distributed denial of service (DDoS).
Securing your API is crucial for protecting your users, data, and reputation.
Here are 6 strategies that can help you out:
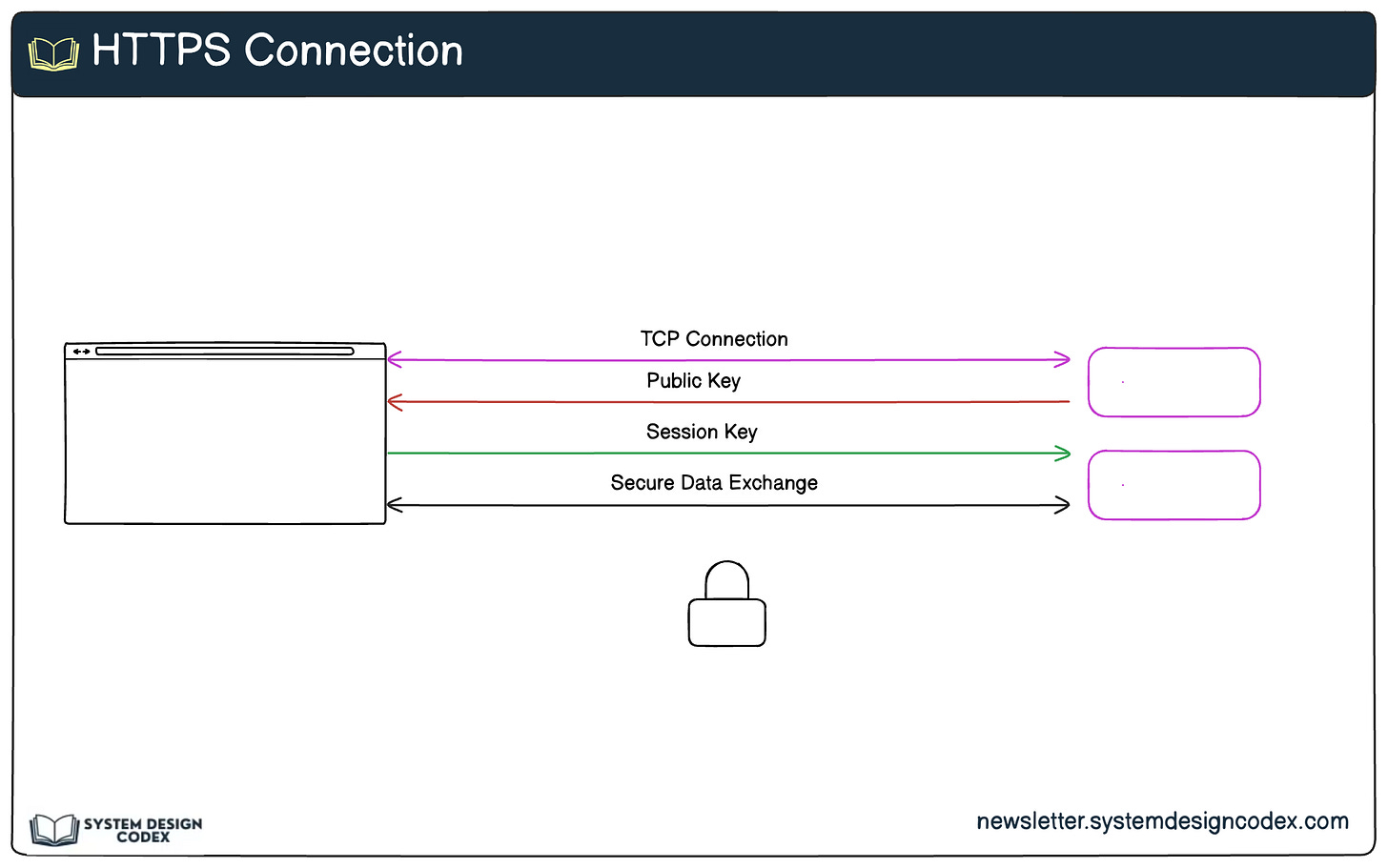
1 - Using HTTPS
The first and most basic step in securing an API is using HTTPS (Hypertext Transfer Protocol Secure). HTTPS encrypts data in transit, preventing attackers from intercepting or tampering with sensitive information.
How It Works:
HTTPS uses SSL/TLS to establish a secure connection between the client and server.
Data exchanged between the two parties is encrypted, ensuring confidentiality and integrity.
Why It’s Important:
Protects against man-in-the-middle (MITM) attacks, where attackers intercept and potentially alter the data.
Builds trust with clients, as browsers and API clients flag non-HTTPS endpoints as insecure.
Best Practices:
Obtain and configure an SSL/TLS certificate from a trusted Certificate Authority (CA).
Regularly update and renew certificates.
Enforce HTTPS by redirecting HTTP traffic to HTTPS.
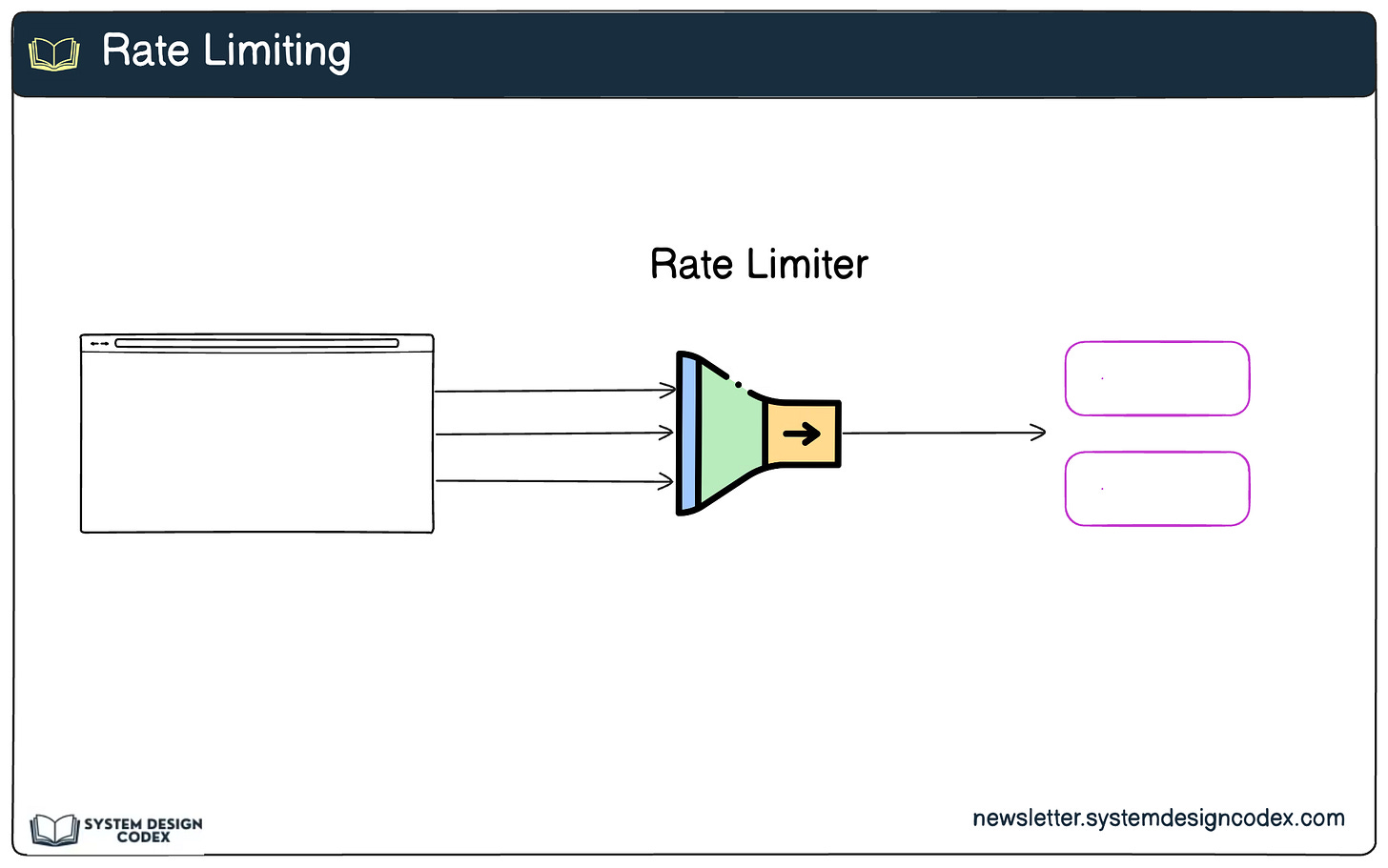
2 - Rate Limiting and Throttling
Rate limiting and throttling are essential strategies for preventing abuse and ensuring the availability of your API. They control the number of requests a client can make within a specific time frame.
How It Works:
Rate Limiting: Restricts the total number of requests a client can make in a given period.
Throttling: Slows down requests once a client exceeds the limit, rather than outright blocking them.
Why It’s Important:
Protects against Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks.
Prevents resource exhaustion, ensuring fair usage across all clients.
Best Practices:
Implement rate limiting at the API gateway or load balancer level.
Use tools like AWS API Gateway, Kong, or Apigee to enforce rate limits.
Provide appropriate error responses (e.g., HTTP 429 Too Many Requests) to inform clients of limits.
Allow customization of rate limits for premium or trusted users.
3 - Validation of Inputs
Proper validation of inputs is critical for defending against attacks such as SQL injection, XML injection, and other data manipulation exploits. APIs must validate all incoming data, including headers, query parameters, and payloads.
How It Works:
Input validation ensures that the data sent by the client adheres to the expected format and constraints.
Rejects invalid or malicious inputs before processing.
Why It’s Important:
Prevents attackers from injecting harmful code or exploiting vulnerabilities.
Ensures API stability and prevents unexpected errors.
Best Practices:
Use libraries or frameworks that support input validation (e.g., Joi for Node.js, Marshmallow for Python).
Implement whitelisting: Allow only specific, predefined formats.
Validate headers, query parameters, JSON payloads, and file uploads.
Reject or sanitize inputs that contain special characters or exceed length limits.
4 - Authentication and Authorization
Authentication and authorization are two cornerstones of API security:
Authentication: Verifies the identity of a user or system.
Authorization: Determines what actions or resources the authenticated user can access.
Best Practices for Authentication:
Use JSON Web Tokens (JWTs) for stateless authentication:
JWT Secret: Use a strong, random secret key for signing tokens.
Token Expiration: Set short expiration times and refresh tokens when necessary.
Secure JWTs using algorithms like HMAC SHA-256.
Avoid using Basic Authentication, as it is less secure and transmits credentials in an easily decodable format.
Best Practices for Authorization:
Implement OAuth 2.0, a robust standard for access delegation.
Use scopes to define what resources or actions a token allows.
Ensure tokens are validated on every request.
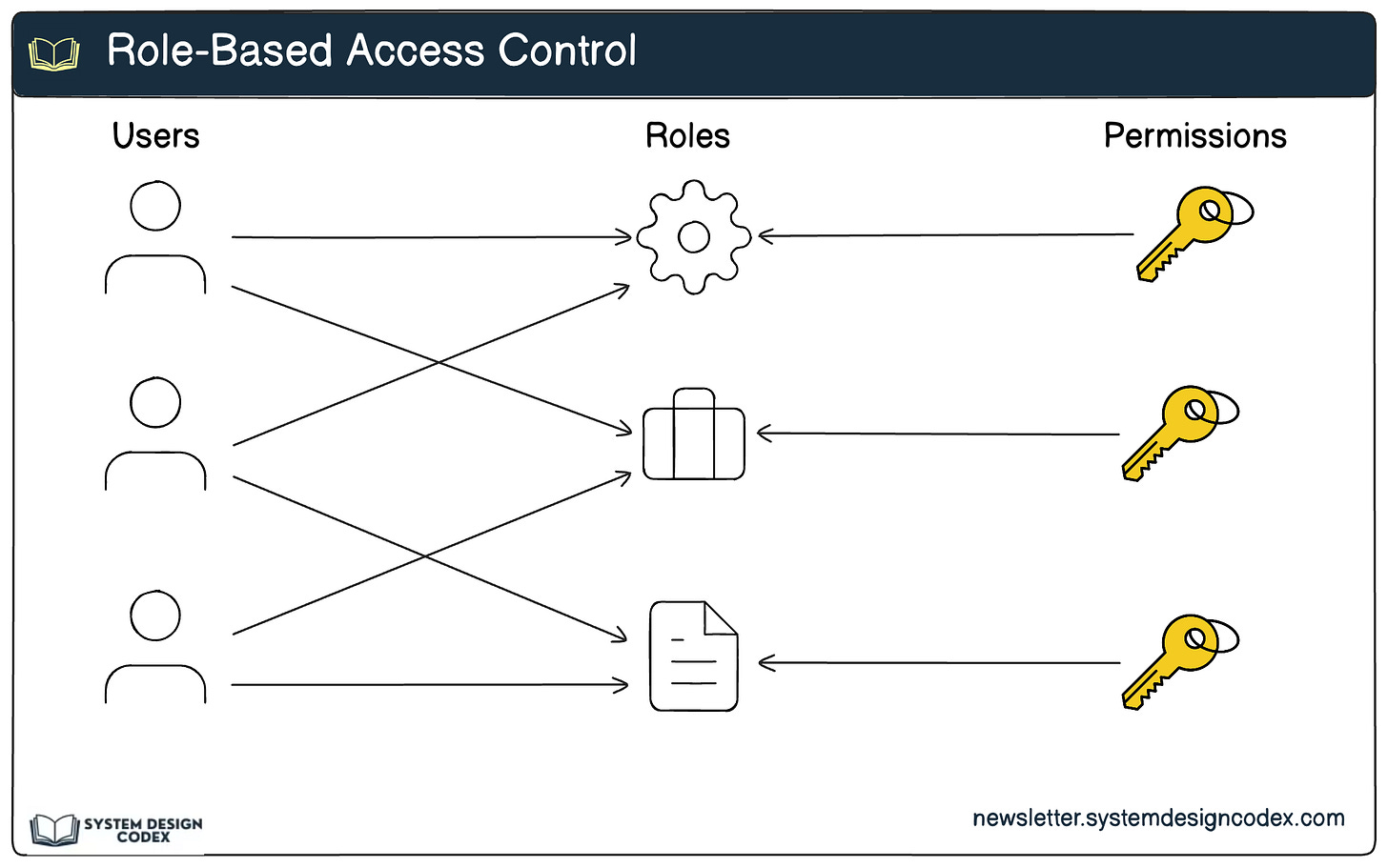
5 - Using Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) simplifies access management by granting permissions based on user roles. For example, an admin user might have more privileges than a standard user.
How It Works:
Assign roles to users based on their responsibilities (e.g., "admin", "editor", "viewer").
Grant permissions to roles, not individual users.
APIs then check a user’s role before performing actions.
Why It’s Important:
Reduces the risk of unauthorized actions.
Simplifies permission management, especially for large teams.
Best Practices:
Define roles and permissions clearly at the design stage.
Use middleware to enforce RBAC rules in your API.
Regularly review and update roles to ensure they align with business needs.
6 - Monitoring and Logging
Monitoring and logging are essential for detecting and responding to security threats and operational issues. By analyzing API activity, you can identify abnormal patterns or potential vulnerabilities.
Why It’s Important:
Helps detect unauthorized access, malicious activity, and unexpected behavior.
Enables rapid debugging and troubleshooting.
Best Practices:
Use monitoring tools like Datadog, AWS CloudWatch, or Prometheus to track API metrics and errors.
Log key events such as authentication attempts, request rates, and errors.
Avoid logging sensitive data like passwords, credit card information, or access tokens.
Set up alerts for suspicious activities, such as repeated failed login attempts or high traffic spikes.
👉 So - which other strategy will you use to build secure APIs?
Shoutout
Here are some interesting articles I’ve read recently:
Transaction Isolation only makes sense if you understand Read-and-Write Anomalies by Raul Junco
7 Cache Eviction Strategies You Should Know by Ashish Pratap Singh
How 65 hours DOING THIS saves you 60 working days per year by
That’s it for today! ☀️
Enjoyed this issue of the newsletter?
Share with your friends and colleagues.



Great article, Saurabh. It’s spot on with API security basics!
I cannot emphasize enough setting rate-limiting mechanisms, even for private APIs.
I learned a hard lesson when an internal consumer scanned my API to build a cache.
Thanks for the shoutout.
It's interesting how some of these may have been a "nice to have" in the past but I consider them a must right now. That shows technology is more robust right now!
Thanks for sharing my article, Saurabh 🙇